In the posts " " we were introduced to semaphores and spinlocks and how they can be used to protect the critical section. Though both are used for the same purpose, their working is completely different from each other. Here are the major differences between the two.
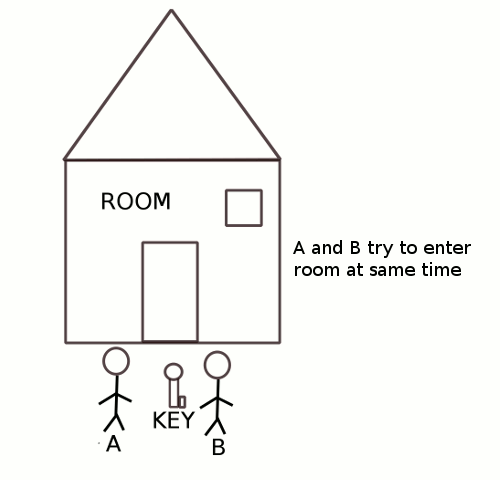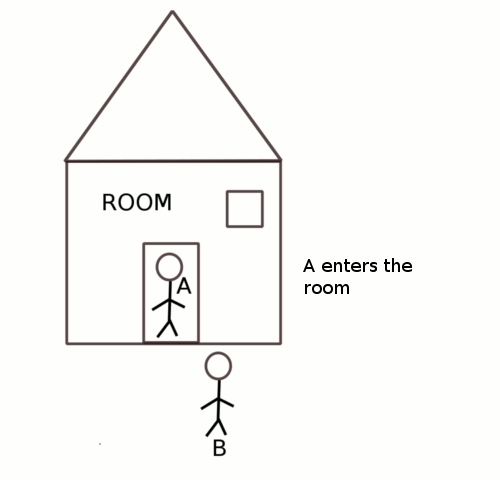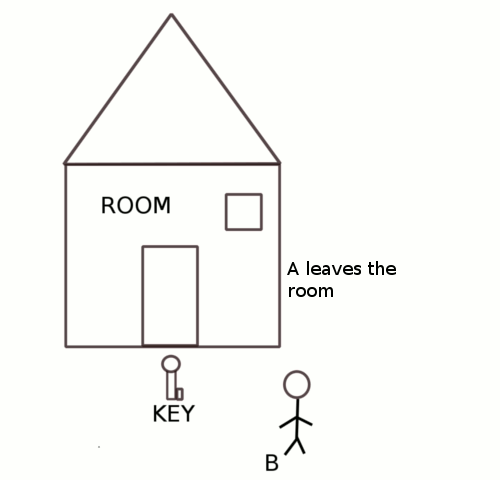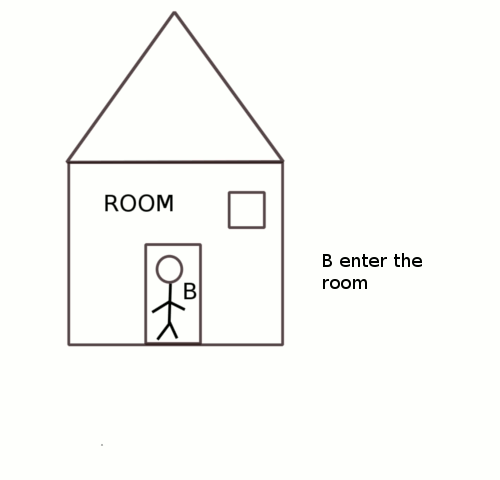
1) Spinlocks can only be used for mutual exclusion, that is it can allow only one process into the critical region at any given time.
In semaphores we can use it for either mutual exclusion or it can be used as counting semaphore to allow more than on process into the critical region.
2) In spinlocks a process waiting for lock will keep the processor busy by continuously polling for the lock.
In semaphores a process waiting for a semaphore will go into sleep to be woken up at a future time and then try for the lock again.
3) In spinlocks a process waiting for lock will instantly get access to critical region as the process will poll continuously fro the lock.
In semaphores the process waiting for a lock might not get into critical region as soon as the lock is free because the process would have gone to sleep and will enter the critical region only when it is waken up.
4) Spinlocks can have only two values LOCKED and UNLOCKED.
Semaphores if used as mutex will have value 1 or 0, but used as counting semaphore it can have different values.
5)Spinlocks are not very useful in uniprocessor systems as they will keep the processor busy while polling for the lock, thus disabling any other process from running.
Semaphores don't keep the processor busy while waiting for the lock thus, they can be conveniently used in a uniprocessor system
6) It is recommended to disable interrupts while holding a spinlock.
Semaphores can he locked with interrupts enabled.
1) Spinlocks can only be used for mutual exclusion, that is it can allow only one process into the critical region at any given time.
In semaphores we can use it for either mutual exclusion or it can be used as counting semaphore to allow more than on process into the critical region.
2) In spinlocks a process waiting for lock will keep the processor busy by continuously polling for the lock.
In semaphores a process waiting for a semaphore will go into sleep to be woken up at a future time and then try for the lock again.
3) In spinlocks a process waiting for lock will instantly get access to critical region as the process will poll continuously fro the lock.
In semaphores the process waiting for a lock might not get into critical region as soon as the lock is free because the process would have gone to sleep and will enter the critical region only when it is waken up.
4) Spinlocks can have only two values LOCKED and UNLOCKED.
Semaphores if used as mutex will have value 1 or 0, but used as counting semaphore it can have different values.
5)Spinlocks are not very useful in uniprocessor systems as they will keep the processor busy while polling for the lock, thus disabling any other process from running.
Semaphores don't keep the processor busy while waiting for the lock thus, they can be conveniently used in a uniprocessor system
6) It is recommended to disable interrupts while holding a spinlock.
Semaphores can he locked with interrupts enabled.